Blockchain - Topologies
Published:
Lesson: 08
Topic: Blockchain
Author: Ashley Rosilier
Up to this point we have referred to blockchains as single, connected chains of blocks where forking is not allowed. This was the first implementation used in Bitcoin and is still the most commonly used arrangement. There is current research, however, exploring other block arrangements including the ability to have multiple chains at the same time.
The following sections describe different types of block arrangement topologies.
Single Chain
Currently, the most common arrangement in blockchain systems is a single chain. Blocks are appended to the chain in chronological order and forking is not allowed. It is possible that two nodes validate a block simultaneously which would cause the chain to fork into two chains, but most systems have a mechanism in place to resolve this conflict. One of the forks will be selected as the official “canon” and the other will be “orphaned”. Orphaned blocks will then have to be re-added to the chain.
One of the ways to moinimize the occurence of the forking scenario is for the system to slow down block validation, such as in the PoW consensus protocol.
Sidechains
In another topological variation, there is a primary blockchain, called the “main chain” that interacts with other, independent but synchronized blockchains, called “sidechains.” In this scenario, transactions can occur between the blockchains by transferring tokens to and from the main chain and one or more sidechains by use of a “two-way peg.” The main chain and the side change can have completely different consensus protocols and can even be on different platforms.
Sidechanining is useful to enhance scalability of traditional blockchain systems by allowing connections between disparate systems. Assets from the main blockchain can be used to access features or funcdtions on the sidechain which expands functionality of the overal system. Another advantage is that any malicious activity on a sidechain can be isolated from the main chain.
A drawback to sidechaining, however, is that the system is potentially vulerable to attack if one of the sidechains is significantly weaker than the main chain. This weakenss can be used to compromise the entire system. To prevent this scenario, the hash rate difficulty can be held uniform throughout the system to avoid the development a weaker chain.
Multi-Layer
Some of the major challenges with the traditional single chain topology are the latency in adding new blocks and the high processing cost required to participate in the system. These are critical issues in some newer applications of blockchain, such as the Internet of Things (IoT), where participating nodes may lack substantial compute resources and also require realtime feeedback. These are some of the challenges that have led to new topologies comprised of multiple layers of nodes who participate in the blockchain to different degrees.
For example, an IoT network can be divided into “edge layers” and “high-level layers” with separate blockchain implementations for each. The edge layer devices, such as sensors on a local network, have their own blockchain particular for their needs which can in turn can be viewed as a node on the high-level blockchain that pulls the system together.
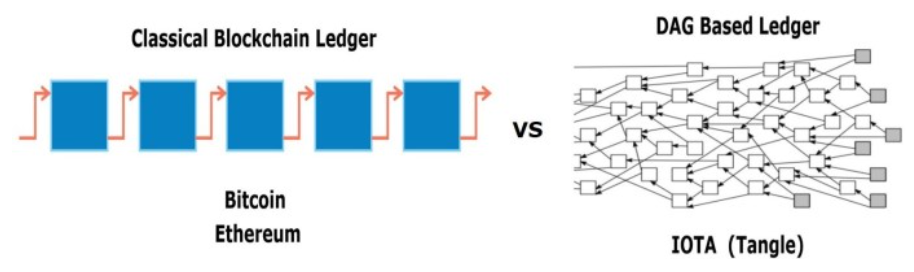
Directed Acyclic Graph
Yet another topology varient are Directed Acyclic Graphs (DAG) which is a version of blockchain that allows, even encourages, forking. In this system, new blocks are added immediately to the blockchain but in order to add a new transaction, a node must first validate two previous transactions. This greatly increases the transaction speed of system, but it does come at a cost to synchronicity. At any given moment each node will have a slightly different view of the tangle while new transactions are propagating through the system. The most prominent DAG implementation is IOTA which uses the Tangle consensus algorithm.
The image below from [18] illustrates the difference between single chain and DAG blockchain networks.
References
[6] M. S. Ali, M. Vecchio, M. Pincheira, K. Dolui, F. Antonelli and M. H. Rehmani, “Applications of Blockchains in the Internet of Things: A Comprehensive Survey,” in IEEE Communications Surveys & Tutorials, vol. 21, no. 2, pp. 1676-1717, Secondquarter 2019, doi: 10.1109/COMST.2018.2886932.
[15] Amritraj Singh, Kelly Click, Reza M. Parizi, Qi Zhang, Ali Dehghantanha, Kim-Kwang Raymond Choo, Sidechain technologies in blockchain networks: An examination and state-of-the-art review, Journal of Network and Computer Applications, Volume 149, 2020, 102471, ISSN 1084-8045, https://doi.org/10.1016/j.jnca.2019.102471.
[16] Xuan S, Zhang Y, Tang H, Chung I, Wang W, Yang W. Hierarchically Authorized Transactions for Massive Internet-of-Things Data Sharing Based on Multilayer Blockchain. Applied Sciences. 2019; 9(23):5159. https://doi.org/10.3390/app9235159
[17] N. Živi, E. Kadušić and K. Kadušić, “Directed Acyclic Graph as Tangle: an IoT Alternative to Blockchains,” 2019 27th Telecommunications Forum (TELFOR), 2019, pp. 1-3, doi: 10.1109/TELFOR48224.2019.8971190.
[18] M. Bhandary, M. Parmar and D. Ambawade, “A Blockchain Solution based on Directed Acyclic Graph for IoT Data Security using IoTA Tangle,” 2020 5th International Conference on Communication and Electronics Systems (ICCES), 2020, pp. 827-832, doi: 10.1109/ICCES48766.2020.9137858.
