Internet of Things - Challenges
Published:
Lesson: 4
Topic: IoT
Author: Ashley Rosilier
There are several challenges in IoT that are the focus of much current research. Here are a few scenarios that highlight some of these challenges:
- Amazon Alexa
- When a verbal command is given, it must be decoded and analyzed for meaning
- The response should be in real time back to the user
- Security is important since instructions might involve purchases on the user’s account
- Autonomous vehicle
- The vehicle can generate 1 GB of data/second that must be analyzed
- Real-time responsiveness is imperitive in order to make correct driving deicisons
- Security is vital since driving decisions can have deadly consequences
Device Limitations
One of the key challenges for IoT systems is the nature of the devices themselves. Most devices are designed to be very small and lightweight, and many are portable. Battery life is often an important consideration, so the device needs to be designed to use as little power as possible. The physical space is also generally small and does not allow room for powerful CPUs or extensive memory capacity. [5]
For these reasons, data storage and processing are generally not done on the device itself, but rather sent to a remote server. In the example of Alexa, for example, the voice comand has to be sent to the cloud in order for it to be translated into machine commands and a response sent back to the user.
The resource limitations also mean that there is insufficient ability for the device itself to handle advanced security and privacy algorithms. This decentralization is a significant challenge as the IoT applications become more and more diverse and integrated into daily human life.
IoT Challenges
As IoT platforms become more prevalent and diverse, a number of critical challenges have arisn that are the focus of curent research. [6]
- Cybersecurity
This is probably the most critical challenge facing IoT currently as devices are very vulnerable to malicous attacks. As mentioned previously, the devices themselves are resource constrained, so they are not able to implement advanced security frameworks. In addition, they are connected with other devices and the Internet so there are numerous ways that attacks can inflitrate the system.
- Privacy
The volume of data being collected by IoT devices is growing exponentially, and much of it would be consdidered sentitive information. Exposing this data to third parties via the IoT platform may violate the user’s consent and make it difficult to control access.
- Massive Data Management
Any IoT system must be scalable in its ablity to handle the massive growth in data volume and network utilization.
- Lack of Standardization and Interoperability
The number of different organizations, governments, alliances and companies involved in defining IoT stamdards has created a hugely heterogenous enviornment with a lack of standardizatoin and interoperability.
Cloud versus Edge Computing
An important aspect of IoT is the ability to have real-time responsiveness based on information received by sensing devices. In addition, the amount of data generated by sensors can be extremely large. The IoT devices themselves, however, are resource-constrained and do not have the memory or CPU capacity to handle these demands. This requires that data storage and processing be done off-device, ie data is sent to a remote server for storage and processing and results are returned back to instruct the device on future behavior. It should be noted, too, that some of the data might be sensitive, so sending it to a remote server requires pricacy and security measures.
Cloud computing has been beneficial in numerous domains due to the ability to access much larger compute resources than would be possible on local server. In the IoT domain, however, he network delays and security risks of sending large amounts of sensitive data back and forth to/from the cloud are too great of a sacrifice. In addition, the resource-contrained IoT devices can often not afford the energy expendature of wireless communiation which makes it impractical to send larges amounts of data to/from the cloud. These factors have lead to the prevalence of edge computing in IoT, where the data is stored and processed as close to the device as possible.
Edge conmputing refers to an architecture were computation is performed at the “edge” of the network, that is between the Iot devices and the cloud. The two diagrams below from [7] illustrate the differnce between the two paradigms.
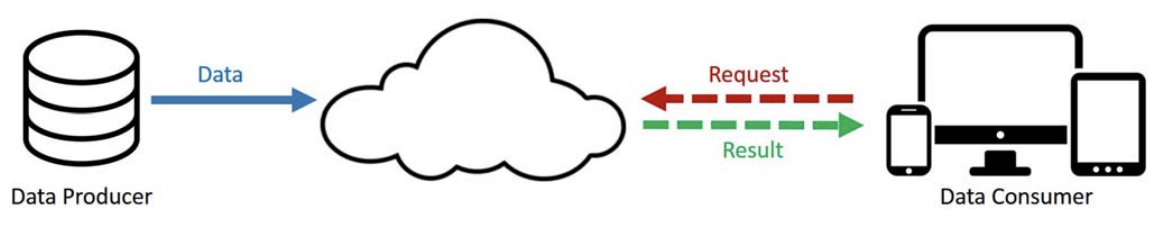 Figure 1 - Cloud Computing Paradigm
Figure 1 - Cloud Computing Paradigm
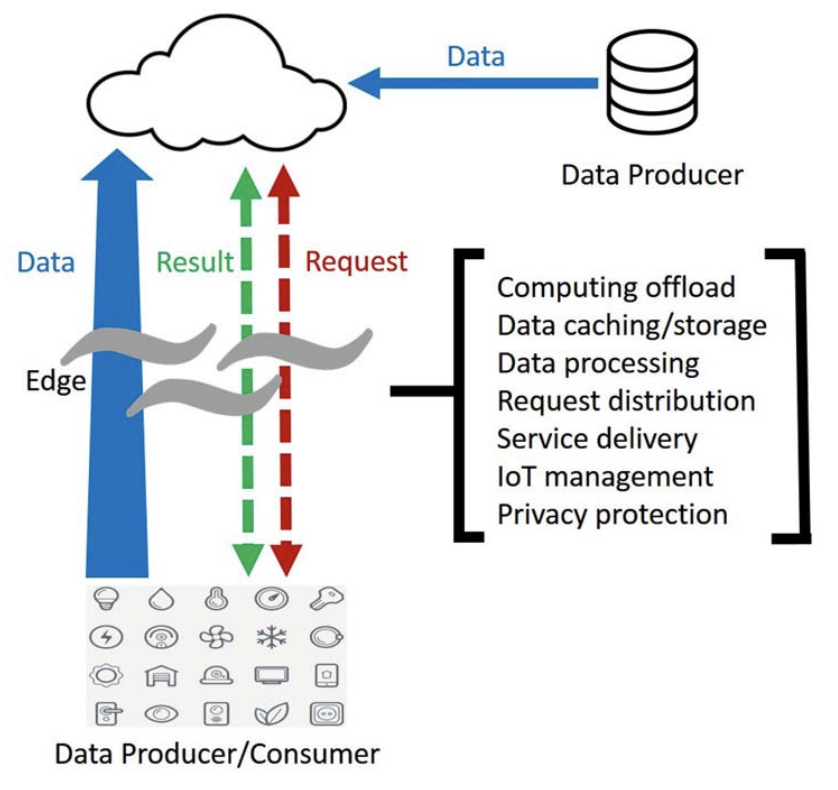 Figure 2 - Edge Computing Paradigm
Figure 2 - Edge Computing Paradigm
References
[5] Honar Pajooh H, Rashid M, Alam F, Demidenko S. Hyperledger Fabric Blockchain for Securing the Edge Internet of Things. Sensors (Basel, Switzerland). 2021 Jan;21(2). DOI: 10.3390/s21020359.
[6] M. S. Ali, M. Vecchio, M. Pincheira, K. Dolui, F. Antonelli and M. H. Rehmani, “Applications of Blockchains in the Internet of Things: A Comprehensive Survey,” in IEEE Communications Surveys & Tutorials, vol. 21, no. 2, pp. 1676-1717, Secondquarter 2019, doi: 10.1109/COMST.2018.2886932.
[7] W. Shi, J. Cao, Q. Zhang, Y. Li and L. Xu, “Edge Computing: Vision and Challenges,” in IEEE Internet of Things Journal, vol. 3, no. 5, pp. 637-646, Oct. 2016, doi: 10.1109/JIOT.2016.2579198.
